At work, I had a task to perform a quick compromise assessment for a hacked Windows server and I got a bunch of etvx files from the suspected host for analysis. I run Linux Mint + i3-gaps and its much easier and productive performing forensics from a Linux machine than Windows in my honest opinion. This post is meant for Linux users who want to perform Digital Forensics to find IOCs from Windows artifacts such as event logs / evtx files. Here my setup for forensics analsys for windows from a Linux perspective and the tools that I use.
Here are some tools that will come handy:
apt update && apt install git vim tar jq libxml2-utils source-highlight -ySigma Rules:
Get the latest sigma rules:
cd ~/
git clone https://github.com/SigmaHQ/sigma
git clone https://github.com/sbousseaden/EVTX-ATTACK-SAMPLES.gitChainsaw:
– Install chainsaw:
wget https://github.com/WithSecureLabs/chainsaw/releases/download/v2.9.1-2/chainsaw_x86_64-unknown-linux-gnu.tar.gz -O ~/chainsaw.tar.gz
tar zxvf ~/chainsaw.tar.gz
chmod +x ~/chainsaw/chainsawExample: Assume that you have a bunch of evtx files that you want to analyze and you have it in a directory "~/EVTX-ATTACK-SAMPLES/", you can run chainsaw against the directory where the evtx files are stored with the below command:
./chainsaw/chainsaw hunt ~/EVTX-ATTACK-SAMPLES/ -s ~/sigma/ --mapping ~/chainsaw/mappings/sigma-event-logs-all.yml -r ~/sigma/rules– The above will output the findings in stdout.
Now, let say you want to output these in csv for reporting or further analysis, you can run the below:
./chainsaw/chainsaw hunt ~/EVTX-ATTACK-SAMPLES/ -s ~/sigma/ --mapping ~/chainsaw/mappings/sigma-event-logs-all.yml -r ~/sigma/rules/ --csv --output csv-outputsAlternatively, chainsaw also has the option to output in json file. This comes handy if you want to injest into a SIEM tool like Wazuh/Opensearch/ES/Spunk.
/chainsaw/chainsaw hunt ~/EVTX-ATTACK-SAMPLES/ -s ~/sigma/ --mapping ~/chainsaw/mappings/sigma-event-logs-all.yml -r ~/sigma/rules/ --json --output json-outputChainsaw filters and advanced searching:
– Chainsaw has options to search for specific event ids. For example, to search for Login Failures (Windows Event ID = 4625), you use the below command:
./chainsaw search -t 'Event.System.EventID: =4625' windows-log.evtx
– To search for specific strings such as to search for lssas dumps:
./chainsaw search -e "lsass" -i windows-log.evtx
– You can also search an entire directory of evtx files as well:
./chainsaw search -e "lsass" -i ~/EVTX-ATTACK-SAMPLES/– To search for events between two timeframes:
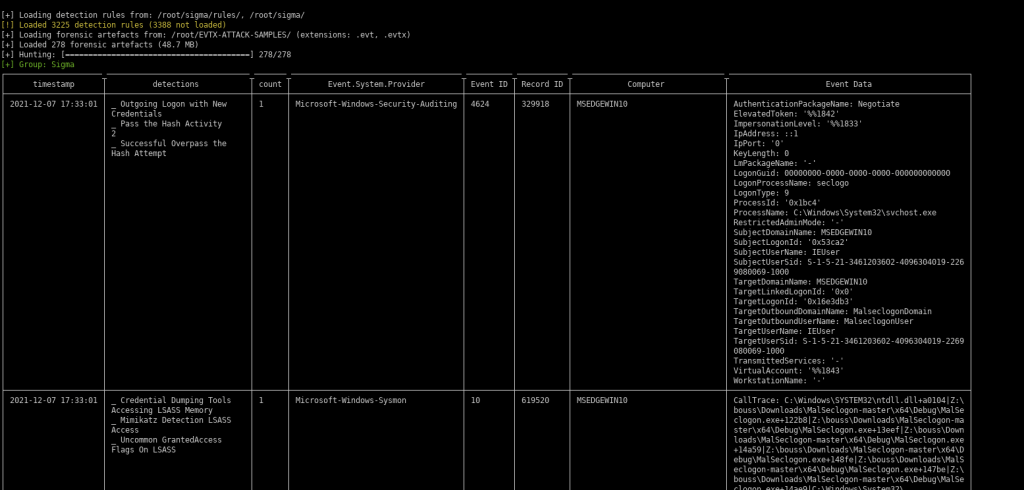
./chainsaw/chainsaw hunt ~/EVTX-ATTACK-SAMPLES/ -s ~/sigma/ --mapping ~/chainsaw/mappings/sigma-event-logs-all.yml -r ~/sigma/rules/ --from "2021-11-01T07:01:00" --to "2022-01-01T07:01:00"– Below is screenshot for reference. (Right click image and open in new tab for better visual)
Evtx Dump:
If you like to dump all the events in a Windows event file for further analysis, there is an awesome opensource tool that allows you to just do that.
wget https://github.com/omerbenamram/evtx/releases/download/v0.8.2/evtx_dump-v0.8.2-x86_64-unknown-linux-gnu -O ~/evtx_dump
chmod +x ~/evtx_dump– To use the dump (Events will be separated with string “Event <count>” in the output file). This is handy when using vim/less by searching for “^Event ” and then using “n” to go the next event.
./evtx_dump-v0.8.2-x86_64-unknown-linux-gnu \
EVTX-ATTACK-SAMPLES/Discovery/4799_remote_local_groups_enumeration.evtx > 4799_remote_local_groups_enumeration.parsed.xml- To generate the dump without the event separators in xml format:
- To generate in json format:
Credits/References:
Chainsaw github
EVTX-ATTACK-SAMPLES
izzyboop
Hope this helps. Happy Hunting Defenders! 🙂
ΞXΤЯ3МΞ