This is a tutorial on how to check checksums of a CentOS image using GPG to verify the integrity of a downloaded CentOS ISO image.
1. Download the public key from the CentOS website
Open a terminal and create a directory where you need to download the ISO and the checksum file.
mkdir validate && cd validate/
Download the GPG public key from the official CentOS website. (You can find the full list of CentOS keys here. )
wget https://www.centos.org/keys/RPM-GPG-KEY-CentOS-Official
Below are the contents of the downloaded file which shows that this is a public key.
cat RPM-GPG-KEY-CentOS-Official -----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v2.0.22 (GNU/Linux) mQINBFzMWxkBEADHrskpBgN9OphmhRkc7P/YrsAGSvvl7kfu+e9KAaU6f5MeAVyn rIoM43syyGkgFyWgjZM8/rur7EMPY2yt+2q/1ZfLVCRn9856JqTIq0XRpDUe4nKQ 8BlA7wDVZoSDxUZkSuTIyExbDf0cpw89Tcf62Mxmi8jh74vRlPy1PgjWL5494b3X 5fxDidH4bqPZyxTBqPrUFuo+EfUVEqiGF94Ppq6ZUvrBGOVo1V1+Ifm9CGEK597c aevcGc1RFlgxIgN84UpuDjPR9/zSndwJ7XsXYvZ6HXcKGagRKsfYDWGPkA5cOL/e f+yObOnC43yPUvpggQ4KaNJ6+SMTZOKikM8yciyBwLqwrjo8FlJgkv8Vfag/2UR7 JINbyqHHoLUhQ2m6HXSwK4YjtwidF9EUkaBZWrrskYR3IRZLXlWqeOi/+ezYOW0m vufrkcvsh+TKlVVnuwmEPjJ8mwUSpsLdfPJo1DHsd8FS03SCKPaXFdD7ePfEjiYk nHpQaKE01aWVSLUiygn7F7rYemGqV9Vt7tBw5pz0vqSC72a5E3zFzIIuHx6aANry Gat3aqU3qtBXOrA/dPkX9cWE+UR5wo/A2UdKJZLlGhM2WRJ3ltmGT48V9CeS6N9Y m4CKdzvg7EWjlTlFrd/8WJ2KoqOE9leDPeXRPncubJfJ6LLIHyG09h9kKQARAQAB tDpDZW50T1MgKENlbnRPUyBPZmZpY2lhbCBTaWduaW5nIEtleSkgPHNlY3VyaXR5 QGNlbnRvcy5vcmc+iQI3BBMBAgAhBQJczFsZAhsDBgsJCAcDAgYVCAIJCgsDFgIB Ah4BAheAAAoJEAW1VbOEg8ZdjOsP/2ygSxH9jqffOU9SKyJDlraL2gIutqZ3B8pl Gy/Qnb9QD1EJVb4ZxOEhcY2W9VJfIpnf3yBuAto7zvKe/G1nxH4Bt6WTJQCkUjcs N3qPWsx1VslsAEz7bXGiHym6Ay4xF28bQ9XYIokIQXd0T2rD3/lNGxNtORZ2bKjD vOzYzvh2idUIY1DgGWJ11gtHFIA9CvHcW+SMPEhkcKZJAO51ayFBqTSSpiorVwTq a0cB+cgmCQOI4/MY+kIvzoexfG7xhkUqe0wxmph9RQQxlTbNQDCdaxSgwbF2T+gw byaDvkS4xtR6Soj7BKjKAmcnf5fn4C5Or0KLUqMzBtDMbfQQihn62iZJN6ZZ/4dg q4HTqyVpyuzMXsFpJ9L/FqH2DJ4exGGpBv00ba/Zauy7GsqOc5PnNBsYaHCply0X 407DRx51t9YwYI/ttValuehq9+gRJpOTTKp6AjZn/a5Yt3h6jDgpNfM/EyLFIY9z V6CXqQQ/8JRvaik/JsGCf+eeLZOw4koIjZGEAg04iuyNTjhx0e/QHEVcYAqNLhXG rCTTbCn3NSUO9qxEXC+K/1m1kaXoCGA0UWlVGZ1JSifbbMx0yxq/brpEZPUYm+32 o8XfbocBWljFUJ+6aljTvZ3LQLKTSPW7TFO+GXycAOmCGhlXh2tlc6iTc41PACqy yy+mHmSv =kkH7 -----END PGP PUBLIC KEY BLOCK-----
2. Check and verify the fingerprint of the downloaded public key.
Using gpg, check the fingerprint of the downloaded public key file using the following command:
gpg --dry-run --import --import-options import-show ./RPM-GPG-KEY-CentOS-Official
pub rsa4096 2019-05-03 [SC]
99DB70FAE1D7CE227FB6488205B555B38483C65D
uid CentOS (CentOS Official Signing Key) <[email protected]>
gpg: Total number processed: 1
From the output, the fingerprint is 99DB70FAE1D7CE227FB6488205B555B38483C65D.
Now, we need to verify if the fingerprint matches the one documented in official CentOS page.
So, go to https://www.centos.org/keys/ and search for the above fingerprint.
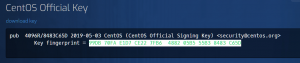
[Note: You could split the fingerprint into blocks of four characters as shown below: 99DB 70FA E1D7 CE22 7FB6 4882 05B5 55B3 8483 C65D ]
If the fingerprint matches the one documented in the official CentOS key documentation page, then the public key is untampered and can be trusted.
[Note: If you are using a newer version of gpg, then you can use “gpg –quiet –with-fingerprint ./RPM-GPG-KEY-CentOS-Official“. I did not use the –with-fingerprint flag as the version of gpg installed in my machine does not show the fingerprints with the –with-fingerprint flag.]
3. Import the Public key to your GNUPG keyring
Now, import the downloaded key to your gnupg keyring.
gpg --import ./RPM-GPG-KEY-CentOS-Official gpg: key 05B555B38483C65D: public key "CentOS (CentOS Official Signing Key) <[email protected]>" imported gpg: Total number processed: 1 gpg: imported: 1
The above shows that it processed and imported 1 key to you local store.
To list the keys currently in your gnupng keyring, you can use the following:
gpg --list-keys /home/r3con/.gnupg/pubring.kbx ------------------------------ pub rsa4096 2019-05-03 [SC] 99DB70FAE1D7CE227FB6488205B555B38483C65D uid [ unknown] CentOS (CentOS Official Signing Key) <[email protected]
4. Download the CentOS ISO image
Download the CentOS ISO file:
wget http://mirrors.piconets.webwerks.in/centos-mirror/8.1.1911/isos/x86_64/CentOS-8.1.1911-x86_64-dvd1.iso
5. Download the CHECKSUM.asc file and verify that it is not tampered with.
Once the download is complete, download the “CHECKSUM.asc” file from the CentOS website:
wget http://mirror.centos.org/centos/8/isos/x86_64/CHECKSUM.asc
If you read the contents of the CHECKSUMS.asc file, you will see that it contains a PGP signed message with the checksums for the CentOS ISO image.
cat CHECKSUM.asc -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256 # CentOS-8.1.1911-x86_64-boot.iso: 625999872 bytes SHA256 (CentOS-8.1.1911-x86_64-boot.iso) = 7fea13202bf2f26989df4175aace8fdc16e1137f7961c33512cbfad844008948 # CentOS-8.1.1911-x86_64-dvd1.iso: 7554990080 bytes SHA256 (CentOS-8.1.1911-x86_64-dvd1.iso) = 3ee3f4ea1538e026fff763e2b284a6f20b259d91d1ad5688f5783a67d279423b -----BEGIN PGP SIGNATURE----- Version: GnuPG v1 iQIVAwUBXh3OvAW1VbOEg8ZdAQihSxAArC0gfNTr0bWPOT/k40lTSoxgDF0qGn4+ d5j9noV3c0Xqd4Um/hxs7ha/qTg82DISYC8+5XHRvU3k156Mxh7dy4FoPopwItoc lpMjnXwDYC/Iptp1XHiD2sun+z+omC2B+DcZergDwrrJzb7CZzxGr84Ztl6Wd54s jCI3dQEsakQUEEuekr3mHtB1R4QHHaRwVwUJSzRQYLF3XiCq788IUaI2sf5kHXsg BxWhzHsBCPG4/FC0ev9ujp5OP/j2FZq4S0cp1+53t/BauyGPOdbvQw71xKsHZQ3J G9TNaFzlAqZJDKpz+XgjQ1V/7kKaFY3dCbxITxbOdSGAMh25cbWd2AamnCFuTzIq vpWY8xWgx6kQ8aLI+VekOYYl4zZswmJBBogXDURCJTqRY6efkT8qhuWVS/obWjBL L3uLL6w4ZkkatUZwglcj2+BhXefAGZgfBExI/xUHFzyXdB8Jv/YwYTTEsREZhf+T 8ggDOOznlUvrNz/atYKwNqAWbC2oY5UXL2OhDznm3lXwQPJG9vZ2Hx6UFpEuuBOR m407o8rfosEbnHgxh9qQ2gnlk+m30VZqhr2dQnOibdY7YtHqk++5snr+yDmXKWDU r08BLy0qGdI8CDxOS0DDb5MmIa5xc2c3w0Jt5q+H9tD7VAlg5uJBju0GwXSsiWHf PlXTxMDETyY= =TBYO -----END PGP SIGNATURE-----
To verify that downloaded “CHECSUMS.asc” file is not tampered and is indeed from CentOS, use the –verify flag.
gpg --verify CHECKSUM.asc gpg: Signature made Tue Jan 14 19:52:52 2020 IST gpg: using RSA key 05B555B38483C65D gpg: Good signature from "CentOS (CentOS Official Signing Key) <[email protected]>" [unknown] gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 99DB 70FA E1D7 CE22 7FB6 4882 05B5 55B3 8483 C65D
The above outputs shows the the signature is good and CHECSUM.asc file is good and not tampered.
At this point, you should have the following files in the directory:
ls -l total 7377932 -rwxrwxrwx 1 r3con r3con 1179 Jun 3 11:10 CHECKSUM.asc -rwxrwxrwx 1 r3con r3con 7554990080 Jan 4 03:17 CentOS-8.1.1911-x86_64-dvd1.iso -rwxrwxrwx 1 r3con r3con 1683 Sep 12 2019 RPM-GPG-KEY-CentOS-Official
6. Verifying the checksum of the downloaded image using the CHECKSUM.asc file.
To verify the checksums of the downloaded ISO image using the following command:
sha256sum -c CHECKSUM.asc 2>&1 | grep OK
CentOS-8.1.1911-x86_64-dvd1.iso: OK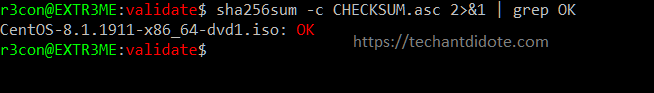
This shows that the checksum matches and the downloaded ISO file is intact or not tampered with.
Hope this helps. Cheers
Source/Credits/References:

Hey,”sha256sum -c CHECKSUM.asc 2>&1 | grep OK” I think that it maybe error.
not CHECKSUM.asc that it is decrypted from private key.CHECKSUM that not decrypt is ok!It is just sha256 checksum.My experiment gets to pass in terminal.
Sorry,That’s encryption.