This guide on how to protect against Off-path TCP vulnerability CVE-2016-5696 in a CentOS 6.8 machine.
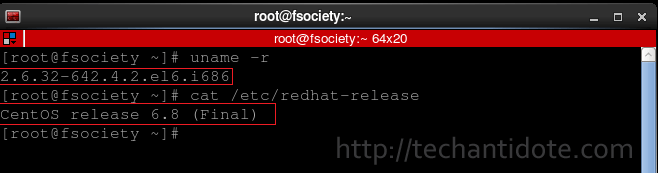
Run the following command to check the kernel version that your box is running:
uname -r
Run the following to verify your Centos version details:
cat /etc/redhat-release
Below is a screenshot for the outputs for the above commands from my CentOS 6.8 box.
Workaround against the attack:
Open your sysctl.conf file:
vi /etc/sysctl.conf
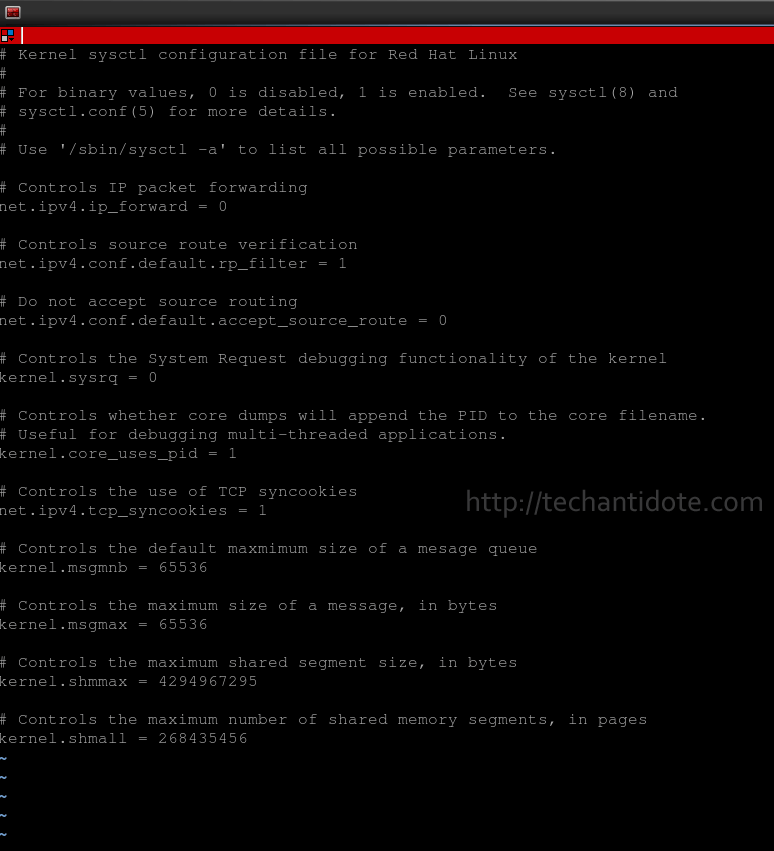
Below is a screenshot of my default sysctl.conf file which does not contain “net.ipv4.tcp_challenge_ack_limit”.
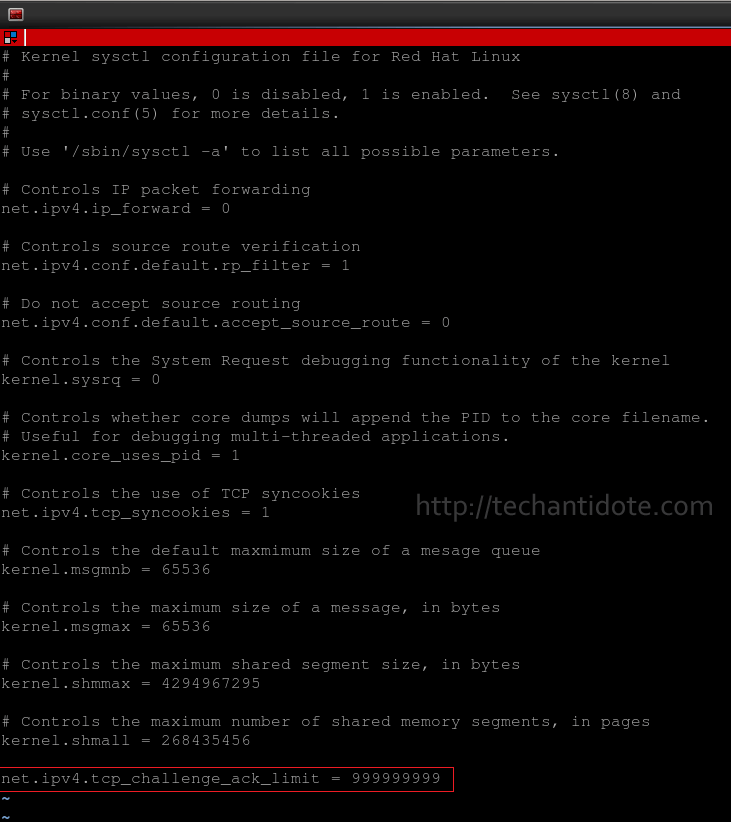
Now add the following line at the end of the config file:
net.ipv4.tcp_challenge_ack_limit = 999999999
Below is a screenshot after editing the config file.
Save and exit the file. (Press ESC and then type :wq and hit Enter in your keyboard).
Use the command below to verify if the value of net.ipv4.tcp_challenge_ack_limit is 999999999.
sysctl -p
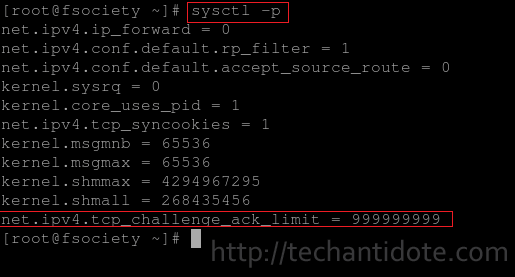
If you are able to see the line in the above screenshot, this means that it will make the exploit extremely hard to perform (practically impossible). The above is a workaround to mitigating the Off-Path TCP attack in a CentOS 6.8 machine and will also work for redhat 6.8.
The Fix:
If you are not looking for the workaround but for a permanent fix, then you can upgrade your Linux kernel to 4.6 or above.
If this article helped you, do leave a comment below and like us on Twitter and Facebook. Cheers!
Source: Bobcares
References: Redhat Portal, Redhat Shared Ack Vulnerability